Cybersecurity is everyone’s problem: An extract from the Keynote of Day 2 at Pass Summit
Wow it’s getting a habit now to write a blog in the later evening about the great PASS Summit currently taking place in Seattle. I simply hope that what I write up here can be useful for anybody else as well…so please give me a short feedback if you like these kind of blog posts or let me know what I could do better.
Note: I have just got to know that Kenneth Fisher has a far more extensive writeup of the keynote. Check his version out at here.
Data is politics and we need diplomats to handle it (at least if things go south)
My day started with the Keynote “Cybersecurity is everyone’s problem” held by Tarah Wheeler. It was a breathtaking session with Tarah teaching me new things about Cybersecurity I have not thought of before and also confirming some thoughts that already ocurred to me.
Tarah just jumped right into the topic with the following statement
Data nowadays is not much different from foreign policy
Data breaches are constant nowadays, political (meaning you need “diplomats” to handle them) and brand new (there is not good training out there)
For clarity I write my own interpretation and thoughts in italics.
Furthermore most companies are scared to acknowledge security breaches. This reminds me of an ongoing discussion in Germany about a reporting obligation for cybersecurity breaches to a government agency. At the same time the government is schizophrenic trying to promote better security via one government agency (BSI) while another agency (Intelligence Agency) tries to leverage security exploits for counter-terrorism-action and therefore has an intrinsic motivation to keep systems insecure and not promoting relevant patches too quickly. So there are talks about a reporting obligation for security breaches but not for a similar obligation regarding security holes.
Three internets
Tarah enlightened me that as of today there are (probably at least) three different internets:
- My home country Germany with the European Union and GDPR regulations
- China with the ability to control what’s accessible on the Chinese Internet and what not
- not to mention the social credit scoring, which goes way farther than anything a data-privacy-concerned european would be able to tolerate
- Tarah mentioned that China does store data with purpose and intent which differs greatly from the approach most US companies undertake namely storing data in order to be able to do something with it later
- The rest of the world (with the US as a large economy)
Fundamental conflicts
You can’t get data security perfect. The only perfect security is for data which does not exist.
GDPR is a wakeup call to companies and it was time for that. However problems come with multiple varying interests. I already described the case about the German BSI striving to provide better information security to everyone meanwhile the Intelligence Agency works to exploit the current state of mostly inadequate information security. The same does happen on other levels as well by law itself: One customer has the perfect right after GDPR to request the deletion of his/her data. However at the same time regulations regarding taxes or telecommunications bind companies to keep exactly the same data around. You could also put it another way reflecting a saying from Star Trek: What does weigh more in the end? The needs of the many or the needs of the few respectively the one individual? Wow…getting quite philosophical at late hours now.


The other discussion about a trade-off is happening within the companies themselves. From a data security perspective trying to minimize the attack surface we might go “Oh my gosh, delete these sensitive data ASAP”. On the other hands we all now want to do sophisticated things like Machine Learning and we just don’t know in advance if it wouldn’t be preferable to have some of these sensitive data to make our ML models better. So Tarah brought up the question we all have to ask ourselves if we are going down that path:
Is the attack surface of that sensitive data potentially greater than the value provided to the business?
And of course that’s quite a tough question and someone worth arguing over.

Last but not least it gets even more complicated by our interconnected global world with different conflicting laws between countries or regions. It does not help thinking about your own countries home turf where your rules apply. Why? Because data has become global a long time ago. As an end user we cannot control the route our data takes through the internet, we might only choose to encrypt it while being transported. It doesn’t help much if data are for example on “German soil treated with German laws” but in the same time are processed completely different in another region on earth.
Tarah concluded her great keynote with an optimistic view in the future: We could leverage quantum cryptography to make data assets more secure while addressing the issue of data privacy and deletes at the same time. Let’s see how that turns out.
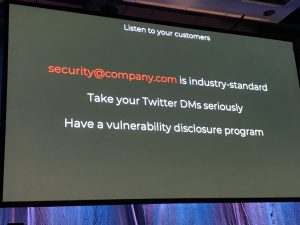
Her call-to-action was the following:
- Check the security-mail-address of your company…if there even is one and who responds
- Be vigilant on security-relevant messages from your network (this might give you some minutes head start on tackling the matter)
- Be sure to be able to disclose your vulnerabilities (hiding and legal debates just make things worse)
It was a distinct pleasure to follow that talk…I do by no means have all the answers or am now a cybersecurity expert but it helps incredibly to drive awareness.